With cybersecurity best practices at the forefront, this paragraph opens a window to an amazing start and intrigue, inviting readers to embark on a storytelling filled with unexpected twists and insights.
Cybersecurity is a critical aspect of safeguarding digital assets and information in today's interconnected world. This article delves into the importance of cybersecurity best practices, common strategies to enhance security, and key considerations for network security and employee training.
Importance of Cybersecurity Best Practices
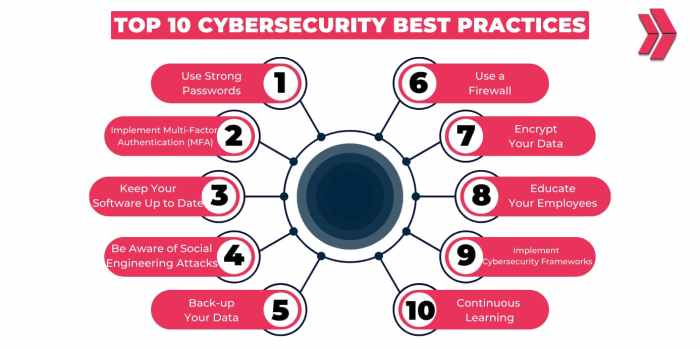
Implementing cybersecurity best practices is crucial in safeguarding sensitive information and protecting against cyber threats. By following established guidelines and protocols, organizations can significantly reduce the risk of security breaches and data compromises.Neglecting cybersecurity best practices can have severe consequences, including financial losses, reputation damage, legal implications, and potential disruptions to business operations.
A single security incident can lead to significant repercussions that may impact an organization's viability and credibility.
Contribution to a Robust Security Posture
Adhering to cybersecurity best practices enhances an organization's overall security posture by establishing a proactive approach to threat mitigation and risk management. By implementing measures such as regular software updates, robust access controls, employee training, and incident response planning, organizations can better defend against evolving cyber threats.
- Regular Software Updates: Keeping systems and applications up to date helps address known vulnerabilities and reduce the likelihood of exploitation by cyber attackers.
- Robust Access Controls: Implementing strong authentication mechanisms and least privilege access policies can limit unauthorized access to critical systems and data.
- Employee Training: Educating staff on cybersecurity awareness and best practices can help prevent social engineering attacks and enhance overall security awareness within the organization.
- Incident Response Planning: Developing and testing incident response plans ensures a prompt and effective response to security incidents, minimizing their impact on operations.
Common Cybersecurity Best Practices

When it comes to cybersecurity, following best practices is crucial to protect your digital assets and personal information from potential threats. Let's explore some widely accepted cybersecurity best practices.
Regular Software Updates
Regularly updating your software is essential in maintaining a secure digital environment. Software updates often include patches for security vulnerabilities that hackers can exploit. By keeping your software up to date, you can prevent cyber attacks and protect your sensitive data.
Strong Passwords and Multi-Factor Authentication
Using strong passwords and implementing multi-factor authentication (MFA) adds an extra layer of security to your accounts. Strong passwords should be unique, complex, and not easily guessable. MFA requires users to provide multiple forms of verification before accessing an account, making it harder for unauthorized individuals to gain entry.
Network Security Best Practices
When it comes to safeguarding sensitive information and preventing unauthorized access, implementing strong network security measures is essential for organizations. By following key network security best practices, businesses can protect their data, systems, and networks from cyber threats.Segmentation is a crucial aspect of network security that involves dividing a network into smaller segments to limit access to sensitive data.
By segmenting the network, organizations can contain potential breaches and prevent attackers from moving laterally across the entire network.
Importance of Encrypting Data in Transit and at Rest
Encrypting data in transit and at rest is vital for maintaining the confidentiality and integrity of information exchanged over a network. When data is encrypted in transit, it is scrambled to prevent eavesdropping and unauthorized interception during transmission. Similarly, encrypting data at rest ensures that information stored on servers or devices remains secure even if physical access is compromised.
- Use secure communication protocols such as SSL/TLS to encrypt data transmitted between devices and servers.
- Implement encryption mechanisms for data stored on servers, databases, and endpoints to protect it from unauthorized access.
- Regularly update encryption keys and algorithms to maintain the effectiveness of encryption techniques against evolving threats.
- Enforce strong password policies and multi-factor authentication to add an extra layer of security for accessing encrypted data.
Employee Training and Awareness
Employee training plays a crucial role in cybersecurity best practices as employees are often the first line of defense against cyber threats. By educating employees on cybersecurity risks and best practices, organizations can significantly reduce the likelihood of a successful cyber attack.Regular security awareness programs are essential in fostering a security-conscious culture within an organization.
These programs help employees recognize potential threats, understand how to respond to incidents, and stay vigilant in protecting sensitive information.
Common Cybersecurity Threats
- Phishing attacks: Emails or messages designed to trick employees into revealing sensitive information or downloading malware.
- Ransomware: Malicious software that encrypts files or systems until a ransom is paid.
- Insider threats: Employees or contractors who misuse their access to steal data or compromise systems.
- Weak passwords: Employees using easily guessable passwords that can be exploited by hackers.
Last Word
In conclusion, adopting cybersecurity best practices is imperative for organizations to mitigate risks and protect against cyber threats. By implementing robust security measures, staying updated on the latest trends, and fostering a culture of awareness, businesses can strengthen their defense mechanisms and safeguard sensitive data effectively.
Q&A
What are some examples of potential consequences of neglecting cybersecurity best practices?
Neglecting cybersecurity best practices can lead to data breaches, financial losses, damage to reputation, and legal ramifications.
Why is segmentation crucial for network security?
Segmentation helps in isolating network segments to contain potential breaches and limit unauthorized access, enhancing overall security.
How can regular security awareness programs benefit organizations?
Regular security awareness programs can educate employees about cyber threats, promote best practices, and cultivate a security-conscious culture within the organization.











